Resources
Decades of data breaches, from Target to Equifax and now T-Mobile, have forced consumers to continue to learn about new data breach attack vectors the hard way—by having their personal information exposed.
An application's attack surface is the sum of all the areas of an application which could be attacked by malicious attackers.
What is an API?
In this episode, Pat explains everything you need to know about them, how that data affects your business, and the importance to protect it.
In this episode, Pat explains everything you need to know about them, how that data affects your business, and the importance to protect it.
APIs are ripe and juicy targets for cybercriminals.
Learn how cybercriminals are exploiting APIs, why the lack of visibility into API traffic is a serious problem for enterprises, and what you and your team should do now to mitigate risk.
Learn how cybercriminals are exploiting APIs, why the lack of visibility into API traffic is a serious problem for enterprises, and what you and your team should do now to mitigate risk.
Closing the Gaps to Ensure API Security
Address API security across the entire API lifecycle.
API Security is one of the Fastest-Growing Segments in Cybersecurity
Beyond the perimeter, applying continuous API scanning.
Application programming interfaces (API) play a vital role in today’s enterprise growth strategies. Fueling new revenue and facilitating new market entry, many organizations rush to deploy APIs as fast as they can, often forgetting or minimizing the potential security risks.
Application programming interfaces (API) play a vital role in today’s enterprise growth strategies. Fueling new revenue and facilitating new market entry, many organizations rush to deploy APIs as fast as they can, often forgetting or minimizing the potential security risks.
Latest trends in API security.
Discusseion on the numerous vulnerabilities that exist with APIs and how companies can update their security strategy and tactics to effectively respond to API-based attacks.
Discusseion on the numerous vulnerabilities that exist with APIs and how companies can update their security strategy and tactics to effectively respond to API-based attacks.
Shifting your security posture for an API-first world.
Zero Trust cybersecurity gets a lot of attention these days where breaches and attacks are increasing and unrelenting. And, failure to act or report now carries legal and financial repercussions.
Zero Trust cybersecurity gets a lot of attention these days where breaches and attacks are increasing and unrelenting. And, failure to act or report now carries legal and financial repercussions.
What you need to know about your APIs.
API observability helps you collect and understand data without needing to define the specifics of the question. Rather than relying on assumptions as to how your APIs should work, observability tells you how they are working.
API observability helps you collect and understand data without needing to define the specifics of the question. Rather than relying on assumptions as to how your APIs should work, observability tells you how they are working.
From WAF to SIEM, SOAR and XDR, understanding the differences between security solutions.
API security is now on the list of CISOs top priorities, highlighting their importance, and the risk that APIs carry. The question is no longer, “Should we consider APIs in our security strategy?” Now, the question is: “How do we secure our APIs, and what tools are best suited for our organization?”
API security is now on the list of CISOs top priorities, highlighting their importance, and the risk that APIs carry. The question is no longer, “Should we consider APIs in our security strategy?” Now, the question is: “How do we secure our APIs, and what tools are best suited for our organization?”
What WAFs and API gateways aren’t doing for API security.
WAFs and API gateways are critical parts of the API infrastructure, can provide a false sense of security: False positives (users as attackers) and false negatives (attackers as users) can only be identified with full packet inspection at runtime.
WAFs and API gateways are critical parts of the API infrastructure, can provide a false sense of security: False positives (users as attackers) and false negatives (attackers as users) can only be identified with full packet inspection at runtime.
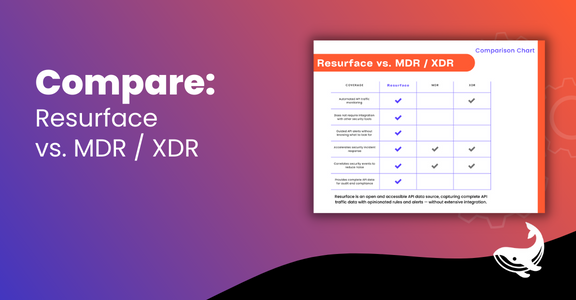
These data aggregation and response systems need API data.
SIEM and SOAR solutions promise one pane of glass for security. But they’re missing critical API data to complete the picture. Capture complete request and response payloads for SIEM and SOAR consumption and fast action.
SIEM and SOAR solutions promise one pane of glass for security. But they’re missing critical API data to complete the picture. Capture complete request and response payloads for SIEM and SOAR consumption and fast action.
Non-API native solutions can’t detect API attacks or failures.
Next gen security solutions consolidate security events, but are only as good as they data they have. Without extensive integrations, these solutions can be expensive shelfware. Resurface is purpose-built for API data - informing you on what matters in real-time.
Next gen security solutions consolidate security events, but are only as good as they data they have. Without extensive integrations, these solutions can be expensive shelfware. Resurface is purpose-built for API data - informing you on what matters in real-time.
Capturing system metrics won’t prevent your next data leak.
Logging events is a critical part of any security strategy, yet just capturing the data isn’t enough, you need to know what to look for. And often, logging solutions carry a significant cost, so API traffic is often turned off, making “insufficient logging & monitoring” a perennial OWASP APITop10.
Logging events is a critical part of any security strategy, yet just capturing the data isn’t enough, you need to know what to look for. And often, logging solutions carry a significant cost, so API traffic is often turned off, making “insufficient logging & monitoring” a perennial OWASP APITop10.
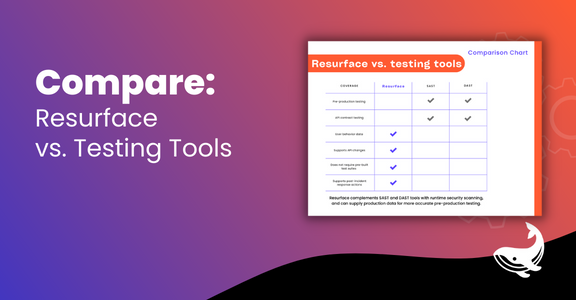
Pre-prod = perfect. Production? Not so much.
Another critical part of APIs, testing for performance and security. But once in the wild, APIs can be used and abused in surprising and unexpected ways. Developers have no way of knowing this without runtime scanning for attacks, vulnerabilities and failures.
Another critical part of APIs, testing for performance and security. But once in the wild, APIs can be used and abused in surprising and unexpected ways. Developers have no way of knowing this without runtime scanning for attacks, vulnerabilities and failures.
Designed to detect and alert on API threats in real-time.
Robust API security requires API-centric solutions that natively understand API traffic, and provide useful guidance at runtime.
Robust API security requires API-centric solutions that natively understand API traffic, and provide useful guidance at runtime.
Providing better insights into what's beneath the surface of API interactions.
To succeed in today's digital economy, organizations in every industry are using APIs to unlock services that connect users, customers, and partners in unprecedented ways. Resurface makes it easy to see, understand, and discover details about every API call.
To succeed in today's digital economy, organizations in every industry are using APIs to unlock services that connect users, customers, and partners in unprecedented ways. Resurface makes it easy to see, understand, and discover details about every API call.




.png)



.png)






.png)
-1.png)